
Auto Generating TLS Certificates for Tanzu Application Platform (TAP) Workloads
Table of Contents
Intro
As part of learning and using Tanzu Application Platform (TAP), I looked into auto generating TLS certificates, for the Workloads I provision.
The full documentation for what I describe in this blog post, can be found here. This blog post, describes how I did it, with with the set of components, that I use.
TAP installs Cert-Manager as part of the installation. Other than being a really cool solution, it also made sense to use that, to generate the certificates I needed.
Solution
To be able to create new certificates, I created a Clusterissuer, that could generate certificates from Let’s Encyrpt, by using DNS validation, via CloudFlares API.
This requires having your domains hosted by Cloudflare, and to generate a API key. It’s easy, and very well decribed in Cert-Managers documentation here.
The first thing I needed to do, was to create a secret, with the API key, to communicate, with Cloudflare.
secret.yaml
apiVersion: v1
kind: Secret
metadata:
name: cloudflare-api-token
namespace: cert-manager
type: Opaque
stringData:
api-token: YOURAPITOKEN
Replace “YOURAPITOKEN” with your own token and run
kubectl apply -f secret.yaml
Then I created the ClusterIssuer, that was going to use that secret
clusterissuer.yaml
apiVersion: cert-manager.io/v1
kind: ClusterIssuer
metadata:
name: letsencrypt
namespace: cert-manager
spec:
acme:
email: YOUREMAIL
server: https://acme-v02.api.letsencrypt.org/directory
privateKeySecretRef:
name: letsencrypt-account-key
solvers:
- dns01:
cloudflare:
email: YOUREMAIL
apiTokenSecretRef:
name: cloudflare-api-token
key: api-token
Replace “YOUREMAIL” with your own email and run
kubectl apply -f clusterissuer.yaml
You should now have the ability to create valid certificates.
The next part, was configuring TAP to do this automaticly.
For this, I needed to update 2 configmaps. I did this by creating the following file
patch-certmanager-tls.yaml
data:
issuerRef: |
kind: ClusterIssuer
name: letsencrypt
Witch I used to update the config-certmanager configmap, by running the following
kubectl patch configmap config-certmanager -n knative-serving --patch-file patch-certmanager-tls.yaml
Then I created
patch-network-tls.yaml
data:
auto-tls: Enabled
http-protocol: Redirected
To set TLS to be autogenerated, and to redirect to HTTPS. And used that to patch onfig-network configmap, by running
kubectl patch configmap config-network -n knative-serving --patch-file patch-network-tls.yaml
And that was it.
All workloads, is now deployed with a valid certificate :-)
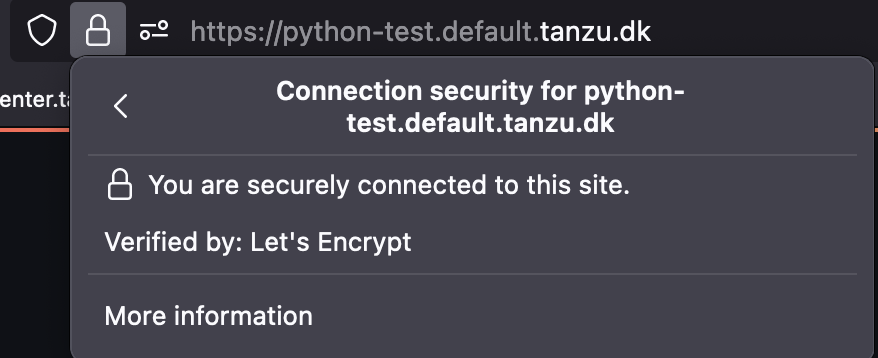
Note if you wan’t Tap-Gui to also use a HTTPS certificate, from cert-manager (You should) then the documentation, on how to do that is found here.
Photo by Bank Phrom on Unsplash