VIBE CODING IS THE NEW FRONTPAGE - AND THAT'S NOT NECESSARILY BAD
Intro
Remember Microsoft FrontPage? If you’re old enough to have been around during the late 90s web development scene, you probably have strong feelings about it. FrontPage was the tool that “democratized” web development - suddenly, anyone could create websites without knowing HTML, CSS, or understanding how the web actually worked.
ARE YOU MODERNIZING OR JUST DOING LIFT AND SHIFT?
This blog post is a repost of the following Linkedin article.
Intro
These days, I see a lot of articles about changing one hypervisor platform for another. The reason is that the old platform, is changing the license terms, so you need to buy xx for xx amount (that makes sense, if you are running any serious workload) Note i’m biased, since I have worked for one of the vendors.
FIX LOADBALANCER SERVICES NOT WORKING ON SINGLE NODE TALOS KUBERNETES CLUSTER
Intro
I’ve started playing around with Talos for my homelab setup. Talos is a modern OS built specifically for Kubernetes, which makes it an interesting option for running clusters.
In my lab, I only have a single Intel NUC that needs to function as both control plane (master) and worker node. This should work fine in theory, but after setting everything up, I ran into an issue with LoadBalancer services.
USING MULTIPLE TRAEFIK INSTANCES ON A SINGLE DOCKER HOST
Intro
I’ve been using Traefik as my reverse proxy of choice for quite some time. It integrates seamlessly with Docker, automatically discovering containers and creating routes based on labels. This makes it incredibly easy to deploy new services without manual configuration.
However, as my setup grew more complex, I found myself wanting to separate my services into different routing groups:
SECURELY EXPOSING SERVICES WITH TRAEFIK AND TAILSCALE
Intro
I’ve been using Tailscale for quite some time now, and it’s one of those tools that just works. It creates a mesh VPN between my devices, making it easy to access services regardless of where I am.
However, I’ve always wanted a cleaner way to access my internal services without remembering IP addresses or using different ports, and with valid certificates.
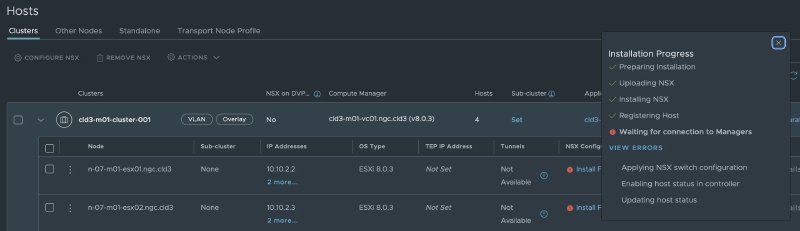
VCF CREATE TRANSPORT NODE COLLECTION FAILS AT 48 PERCENT
The problem
For a clean installation, Cloud Builder fails with the step “Create Transport Node Collection”.
Troubleshooting
Troubleshooting the problems by logging into the NSX manager, revelaled the problem was “Waiting for connection to managers”
So that ment that the hosts were trying to contact the NSX manager, with no luck.
ENHANCE KUBECTL WITH LOCAL AI USING OLLAMA AND OPEN SOURCE LLMS
Intro
I know how to write a Kubernetes Deployment, service, secret or many of the other types you need when working with Kubernetes.
This post is not about that.
It’s about doing it faster and avoiding having to google for things, I can’t remember, at the time when I need it.
RUNNING EXTERNAL DNS WITH CLOUDFLARE
Update
Just after creating this blog post, I submitted a PR to https://github.com/kubernetes-sigs/external-dns/ where I added the things I was missing in the documentation.
I expected it to take weeks, if ever, to get approved. But a couple of hours later, it was merged into the Master branch.
This kinda makes this blog post obsolete. But I will still keep it here, for reference, and maybe as a reminder to fix things at the source, before writing a blog post about it, in the future :-)
ADDING EXTRA VLAN/PORTGROUP TO A TANZU TKGS ENVIROMENT
The problem
I have met several customers, who have vSphere with Tanzu that is struggling to add more than 1 network, to their environment, when they use the AVI Loadbalancer, and not the full NSX solution.
This is a quick guide, on how to do just that. Note it’s only possible (as far as I know), to have 1 network to each vSphere namespace.
FIXING CILIUM ON KIND
Update
It seams that either downgrading Docker engine, to an earlier version or waiting for version 4.27.0 will fix the Cilium problem.
More info can be found in this issue. Thanks to Daniil Bazhanov, for the link/update.
For me, Docker Desktop is gone, and I will test out Colima in my env going forward, and see how that works.